Quick Start
March 7, 2024
Tags:
·
Create an Utho account to try this guide with a $100 credit.
Sign Up
Login or Sign Up
- Go to the Utho Cloud Platform login page.
- Enter your credentials and click Login .
- If you don’t have an account, sign up here.
Accessing Active Sessions
- Open the Utho Cloud Platform dashboard.
- Click on "Activity Logs" from the sidebar.
- You will be redirected to the Activity Logs listing page.
Upon navigating to the Activity Logs Listing Page in Utho Cloud, users will be presented with a detailed table containing all recorded activities. This page serves as a comprehensive view of user interactions and system events within the cloud platform. The table is organized with the following key headers:
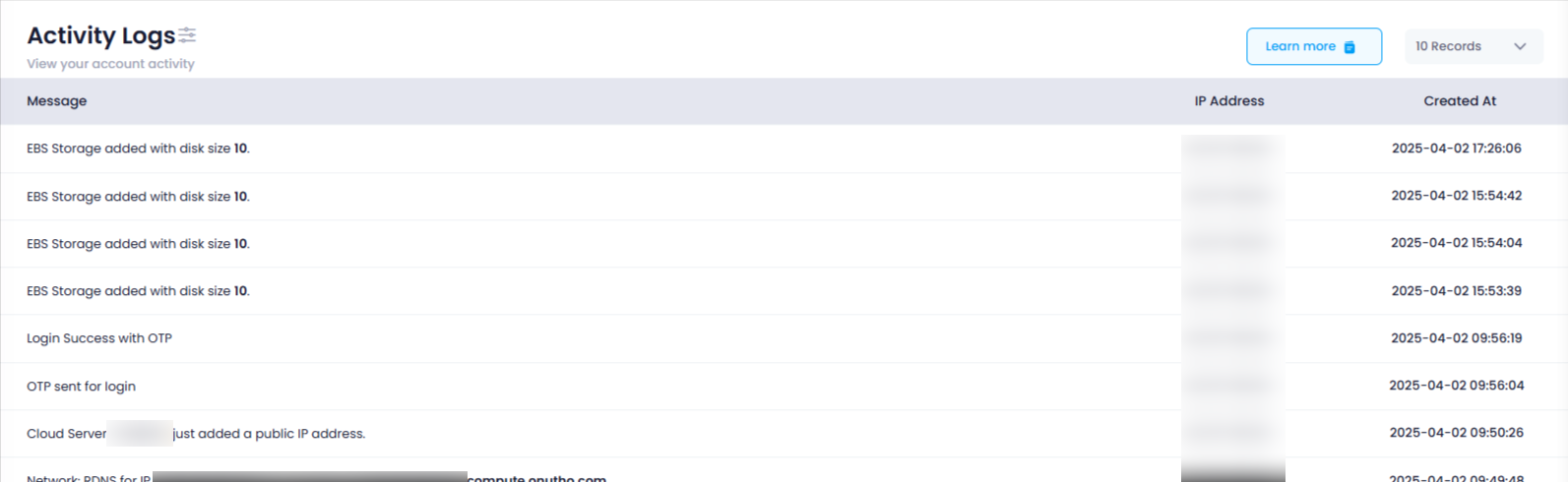
- Message :
- The Message column displays a brief description or summary of the action that was performed during the logged activity. The Message column on the Activity Logs Listing Page is a central component that provides detailed information about the activities performed by users on the Utho Cloud platform. This column captures and displays a brief description of each action or event, offering context and insight into the specific activity that was performed. Each entry in the Message column reflects the nature of the action taken by the user, such as creating or modifying resources, initiating specific services, or performing configuration changes. For example, the Message column may include entries like:
- “User logged in” – Indicates that a user successfully authenticated and accessed the platform.
- “EBS volume created” – Shows that a new Elastic Block Storage volume was provisioned.
- “VM instance started” – Reflects that a virtual machine instance was launched.
- “API call executed” – Documents the use of the platform’s API for interaction or automation.
- “Storage resized” – Indicates that a storage resource was expanded or contracted.
- IP Address :
- The IP Address column shows the IP address from which the action was initiated. This helps track the geographic location or network source of the activity, aiding in security monitoring and identifying unusual or unauthorized access attempts.
- Created At :
- The Created At column records the exact timestamp of when the activity occurred. This provides a chronological order of events, allowing users and administrators to trace actions over time, facilitating auditing and investigation.
Create an Utho account to try this guide with a $100 credit.
Sign Up