Update Firewall
Utho’s firewall feature enables users to configure and manage firewall settings for their cloud server, offering flexibility in network security. A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predefined security rules. Its primary function is to block or allow data packets between your network and external sources (like the internet) to protect against unauthorized access, cyberattacks, and threats. Firewalls can be hardware-based, software-based, or a combination of both. They are commonly used to secure networks by filtering traffic, preventing malicious activities, and ensuring that only authorized users can access certain services or resources.
Attaching a Firewall
Users have the option to attach existing firewalls or create new ones for their cloud server:
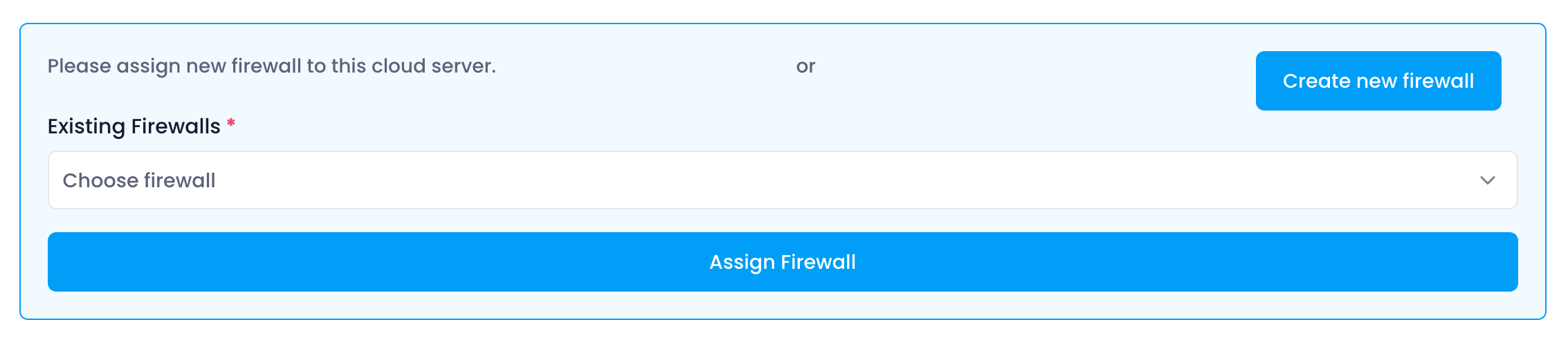
- Attach Existing Firewall : Users can select from a list of pre-existing firewalls and attach one to their cloud server.
- Create New Firewall : If no suitable firewall exists, users can create a new one tailored to their specific security requirements. During the creation process, users define firewall rules and settings to enforce network traffic policies.
Managing Attached Firewalls
Once a firewall is attached to the cloud server, users can:

- View Attached Firewalls : See a list of all firewalls currently attached to their cloud server.
- Detach Firewalls : For each attached firewall, there is an option to detach it from the cloud server. This action removes the firewall’s rules and configuration from affecting the cloud server’s network traffic.
Workflow
- Create or Select Firewall : Depending on the user’s needs, either create a new firewall or select an existing one.
- Attach Firewall : Once chosen, attach the firewall to the cloud server to implement specified security measures.
- Manage Firewalls : Regularly review and manage attached firewalls to ensure optimal security and network performance.
Utho’s firewall management ensures that cloud servers remain secure against unauthorized access and maintain efficient network traffic management according to user-defined policies.